With cybercrime and hacking strategies becoming more complex, enterprises need to be able to trust their users and endpoints more than ever. As a result, the Zero Trust strategy has become an increasingly popular way of protecting enterprise data. Samsung Knox’s trusted security platform and tools are one way to use Zero Trust to protect your enterprise’s data.
How Zero Trust works
Zero Trust is a security strategy that aims to minimize implicit trust in entities that handle enterprise data. With Zero Trust, entities, such as users and endpointsi need to continuously prove their trustworthiness to an enterprise to get access to its resourcesii. For example, just because an enterprise’s VPN authenticates a device, doesn’t mean that the device will be automatically trusted. This approach allows Zero Trust to use dynamic access control.
In contrast to traditional perimeter-based security strategies such as VPNs, dynamic access control dramatically reduces the impact of a compromised endpoint. With perimeter-based approaches, if an attacker compromises a single device or user credential, they can easily breach the entire enterprise network.
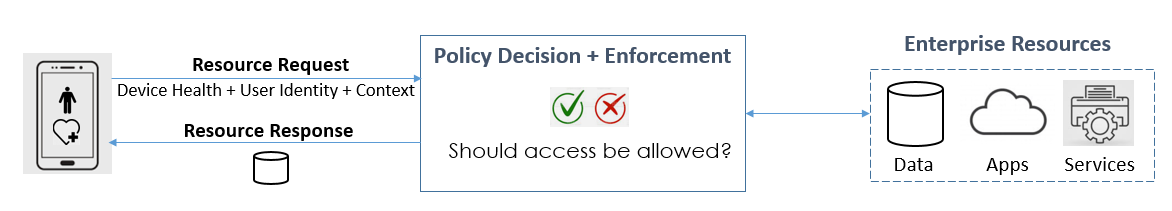
Additionally, Zero Trust allows an enterprise to regulate access to its resources based on a continuous evaluation of contextual information from multiple data sources. This contextual information, or context, takes into consideration sources including user and device identity, device health, location, and frequency of access. For each resource request, a device evaluates the context and sends it to a Policy Decision and Enforcement point (PDP). The PDP then decides whether to allow the endpoint access to the requested enterprise resource. If access is allowed, the requested resource is sent back to the device.
Endpoints: Enabling Zero Trust
When endpoints are involved, there are three principles that a Zero Trust system must uphold. First, the endpoint must collect, evaluate, and protect user data with each request made to ensure that the user has the right credentials to access the system. Second, both the endpoint and system need to continuously evaluate and protect the device from attacks. Finally, the endpoint must regulate access to local and remote resources control on downloaded resources and takes remediation actions as applicable.

Samsung Knox and Zero Trust
The Samsung Knox platform provides a foundation to build an endpoint that can achieve the Zero Trust vision.
Evaluating and protecting user data — User identities are vulnerable to many data breaches. With a recent study finding that phishing and credential stealing were the top two causes of real-world data breaches in enterprises for 2022, protection against these threats has become even more integral for enterprise security.
On the user data end, Samsung Knox can detect and block phishing attempts with the Network Platform Analytics and the Domain Filter firewall. Additionally, Network Platform Analytics lets Samsung Knox identify the exact app a device is making a network request from, providing further confidence to servers that session cookies aren’t stolen and replayed. Other Samsung Knox features such as ARM TrustZone Trusted Execution Environment (TEE) and Knox Vault provide further protection by enabling password-less authentication and token binding standards. For continuous authentication, Samsung Knox’s continuous multi-factor authentication framework allows for the regular collection and interpretation of data to authenticate user identity.
Evaluating and protecting device data — Devices are vulnerable to boot-time and run-time threats such as rooted images, malicious apps, and runtime exploitation.
The Samsung Knox platform has many features that protect device health and identity. To provide verifiable guarantees that only Samsung-authorized platform software components are running on a device, all Samsung Knox devices support trusted boot and Device Health Attestation. To protect against rooting attacks, Samsung Knox deploys features such as the Real-Time Kernel Protection and has parts of its platform, like TrustZone, written in the memory-safe Rust language. Samsung Knox also provides a unique ID and signing key, called the Samsung Attestation Key, for each device. This key can be used with the Knox SDK to generate a certificate that can be used for token binding and verifying a device’s identity to servers.
Samsung Knox also enables the continuous monitoring of endpoint security by providing a variety of contextual information typically used in Zero Trust. The Knox SDK provides access to hundreds of data points spread across the device’s network, kernel, filesystem, and apps for extensive system-wide visibility. Additionally, Samsung Knox allows on-device agents to be notified of and act on changes to device or user data, allowing them to block apps or notify remote PDPs to cut off access to enterprise resources.
Regulating access to local and remote resources — Once resource access is granted, the endpoint has to regulate access to local on-device and remote resources following the Zero Trust principles of least privilege and fine-grained access control. The endpoint also needs to take protective measures if it detects suspicious user or device behavior.
Samsung Knox supports fine-grained access control to regulate access to local and remote resources. With the Global proxy feature, Samsung Knox provides mechanisms to intercept network flows. To provide fine-grained access control, the Knox Platform for Enterprise (KPE) provides strong local isolation and control over enterprise apps and data. KPE, along with Knox Guard, also provide multiple remediation controls to instantly cut off enterprise resource access.
In summary, through features like continuous authentication, device health and hardware protections, and fine-grained access control, the Samsung Knox platform provides a foundation to build an endpoint that can achieve the Zero Trust vision and provide better security for your enterprise.
Learn more about Samsung’s position on the Zero Trust strategy: Browse the White PaperWhite Paper
i Endpoints are user-facing devices that request access to enterprise resources. Endpoints include laptops, desktops, mobile phones, and tablets. In this article, we use the terms “device” and “endpoint” interchangeably.
ii Enterprise resources include enterprise data, apps, and services such as printers.
